Search another article?
Microsoft CA
This article will explain how to create a Microsoft CA in order to use LDAPS protocol and access to SGBox with your AD Users. It’s not mandatory have a Microsoft CA to use LDAPS protocols, you can use also an External CA. The only requirements is that SGBox is able to solve the common name wrote in the certificate.
1. Install the Certificate Services (a “roles” of Server Manager) and configure it creating a root CA by following the wizard. I’ll be required restart the domain controller/server at the end of the task;
2. Test your LDAPs (with a tool link Microsoft LDP). Set DC IP, choose port 636, and flag “SSL” option.
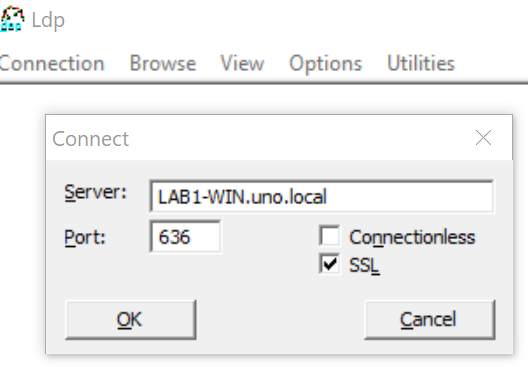
3. If it works, you’ll receive a response like the following:
ld = ldap_sslinit("LAB1-WIN.uno.local", 636, 1);
Error 0 = ldap_set_option(hLdap, LDAP_OPT_PROTOCOL_VERSION, 3);
Error 0 = ldap_connect(hLdap, NULL);
Error 0 = ldap_get_option(hLdap,LDAP_OPT_SSL,(void*)&lv);
Host supports SSL, SSL cipher strength = 256 bits
Established connection to LAB1-WIN.uno.local.
Retrieving base DSA information... (...)
4. Export the domain controller certificate using the following steps:
- From MMC console, add the snap-in Certificate (Local Computer);
- Choose the Personal/Certificates directory;
- choose your certificate (in the Issued To column find the Domain Controller FQDN);
- Right click on the cerficate, and choose the All Tasks/Export option;
- export the certificate in DER o Base-64 formant, and call it “certificate.cer”.
The certificate will be used to a secure communication with the domain controller.
SGBox need the *.crt extention so you need to convert it in the following way from a Linux/Unix machine:
openssl x509 -inform DER -in certificate.cer -out certificate.crt



