Search another article?
Before you begin
If you started with SGBox from version 5.3.0 or above and/or if you have never installed the old SGBox Windows packages Windows package Base and Windows package Advanced, you don’t need to cleanup anything; just follow the standard installation steps.
However, if you’re an old SGBox customer, or if you’ve installed one or both of the old packages, a little cleanup procedure needs to be followed to avoid duplicate events. Please follow the instruction at the end of the “Windows Audit package installation” section.
Windows Audit package installation
To install the new Windows Audit package From SCM->Application->Packages find the package in the package list, click the Install button and then the Download and install button on the App Installation pop-up.
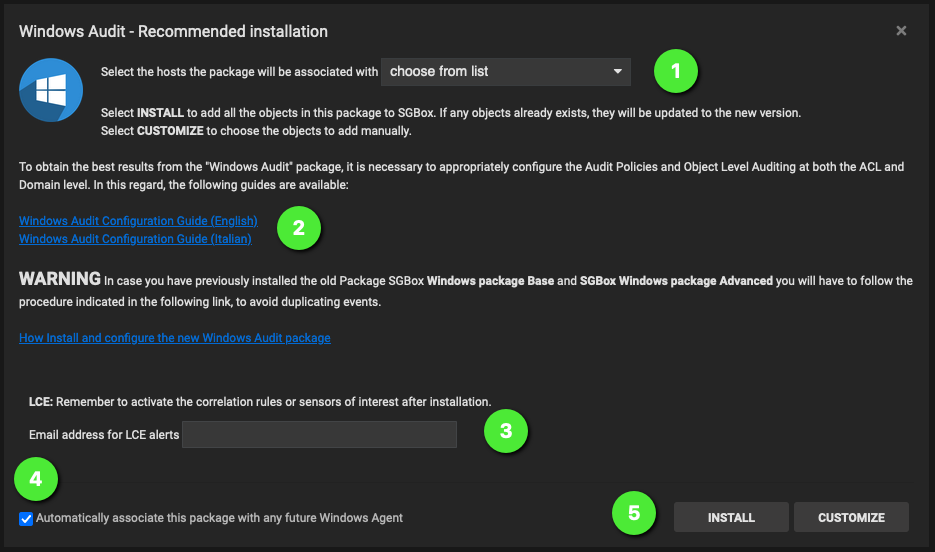
On the Windows Audit – Recommended installation panel, configure installation option as for your needs:
- Select the hosts from which you want to collect Windows Audit information from. These hosts will be automatically added to the Windows Audit Classes, so events collection can immediately start after the installation.
- Download the Group Policy configuration guide and follow the instruction to properly enable needed events collection.
- Insert the email address to which you want to forward LCE alert messages to.
- Check the flag if you want to have newly added/installed windows machines automatically added to SGBox Windows Audit classes.
- Click Install button to install the package.
To check the installation, please verify the existence of the following:
| Dashboard | Windows Audit – Directory Service Group Policy Activities Windows Audit – Directory Service Object Activities Windows Audit – Directory Service Object moved or undeleted Windows Audit – Failed Logon Events Windows Audit – Logon Activities Windows Audit – PnP Device Activities Windows Audit – Security Group Management Windows Audit – Security Group Members Activities Windows Audit – Security Users Events Windows Audit – Session Activities Windows Audit – User Account Management |
| New Classes | Windows Audit – Directory Service Windows Audit – Logon Activities Windows Audit – Security Group Management Windows Audit – User Account Management Windows Audit – Windows Systems Windows Audit – Security Events Windows Audit – Security Log LCE Windows Logon Anomalies LCE Windows Security Events LCE Windows User Anomalies |
| Correlation Rules | [Win Audit] A disabled user was enabled and fails to logon [Win Audit] A disabled user was enabled and logged on successfully [Win Audit] Account created and deleted in a short time [Win Audit] Account Locked Out [Win Audit] Account logged on to a protected network [Win Audit] Administrative Account Locked Out [Win Audit] Administrative account login to multiple systems in a short time [Win Audit] Administrative Interactive Logon out of hours [Win Audit] Administrative User Password Change [Win Audit] Administrative User Password Change non Working hours [WIN Audit] Administrative User Password Reset [Win Audit] Administrative User Password Reset non Working hours [Win Audit] Administrator access from an Unauthorised workstation [Win Audit] Administrator access from an Unauthorised workstation (out of hours) [Win Audit] Event Log Backup [Win Audit] Event Log Service Error [Win Audit] Event Logging Service Shutdown [Win Audit] Failed logon to a disabled account [Win Audit] Failed logon to an expired account [Win Audit] Multiple failed logon for the same user [Win Audit] Multiple failed logon from the same IP [Win Audit] Multiple failed logon on the same host [Win Audit] Multiple logon failed followed by a successful one (same User same SourceIP same Host) [Win Audit] Multiple logon failed followed by a successful one (same User same SourceIP) [Win Audit] Multiple logon failed followed by a successful one (same User) [Win Audit] Multiple logon for the same account in short time [Win Audit] Multiple logon from the same IP Address in short time [Win Audit] Multiple logon with different accounts from the same IP address [Win Audit] Possible Password Spray Attack [Win Audit] Probable Kerberoasting Attack (RC4 Ticket Encryption) [Win Audit] Probable Pass-the-Hash Attack [Win Audit] Security Log Cleared [Win Audit] Security Log Full [Win Audit] System Audit policy change [Win Audit] Unauthorised account logged on out fo hours [Win Audit] Unauthorised Account logged on to a protected network [WIN Audit] User added to Domain Admins Group [Win Audit] User added to Enterprise Admins Group [Win Audit] User added to Global Group [Win Audit] User added to Local Group [Win Audit] User added to Universal Group [Win Audit] User Interactive Logon out of hours [Win Audit] User Removed from Global Group [Win Audit] User removed from Local Group [Win Audit] User removed from Universal Group [Win Audit] User added to a Global Group and removed in a short time [Win Audit] User added to a Local Group and removed in a short time [Win Audit] User added to a Universal Group and removed in a short time |
| Sensors | [Win Audit] High number of Failed logon (same IP) [Win Audit] High number of Failed logon (same User) [Win Audit] High number of Failed logon (same Workstation) [Win Audit] High number of Locked Out Users (same Domain) |
| Multiclass Templates | [Win Audit][Dash] Directory Service GPO activities [Win Audit][Dash] Directory Service Object Activities [Win Audit][Dash] Directory Service Object moved or undeleted [Win Audit][Report] Account Created [Win Audit][Report] Account Deleted [Win Audit][Report] Account Disabled [Win Audit][Report] Account Enabled [Win Audit][Report] Account Locked Out [Win Audit][Report] Account Logon Failed [Win Audit][Report] Account Logon/Logoff [Win Audit][Report] Account password Changed [Win Audit][Report] Account Password Reset [Win Audit][Report] Account Unlocked [Win Audit][Report] Directory Service GPO Activity [Win Audit][Report] Global Group Created [Win Audit][Report] Global Group Deleted [Win Audit][Report] Local Group Created [Win Audit][Report] Local Group Deleted [Win Audit][Report] Member Added to Global Group [Win Audit][Report] Member Added to Local Group [Win Audit][Report] Member Added to Universal Group [Win Audit][Report] Member Removed from Global Group [Win Audit][Report] Member Removed from Local Group [Win Audit][Report] Member Removed from Universal Group [Win Audit][Report] sAM Account Name Changed [Win Audit][Report] Universal Group Created [Win Audit][Report] Universal Group Deleted [Win Audit][Report] USB External device mounted [Win Audit][Report] USB External DiskDrive mounted |
| Windows Agent Configuration | Audit – Logon Activity Audit – Security Group Management Audit – Security Log Audit – User Account Management Audit – Directory Service Audit – Windows Systems Audit – Security Events |
Post installation considerations
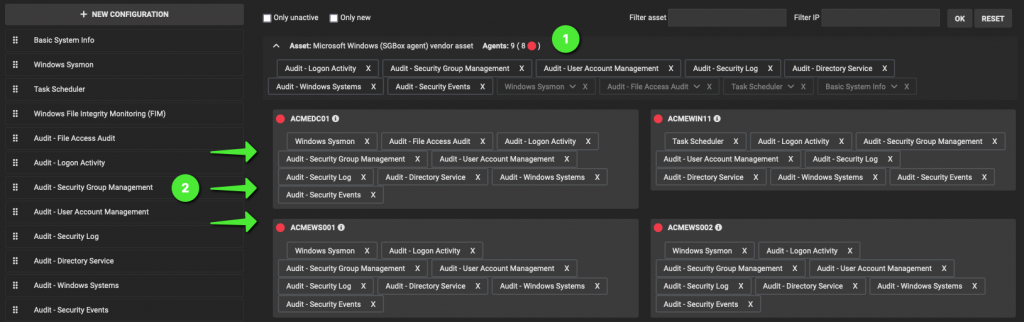
We need also to make sure that the new Windows Agent Configuration are correctly bound to the relative windows hosts. Go to LM->Configuration->Agents and check that everything is fine.
Open the Microsoft Windows (SGBox agent) Asset (1) and verify that all the needed “configurations” (2) are properly assigned to to your Windows devices. Don’t forget to click the Save Changes button, in the bottom-left corner, if you did any change.
To eventually force the system to push configurations to the Agents, simply remove and newly add a Configuration from a device of your choice, and finally click the Save Changes button.
Please note that for events collection to be effective, it is necessary to appropriately configure both the Group Policies and the Object-level Access auditing. Here below the link to the configuration guide:
- Windows-Auditing-Configuration-Guide-v1.2_EN.pdf (1443 downloads )
- Windows-Auditing-Configuration-Guide-v1.2_IT.pdf (1480 downloads )
Old Windows package cleanup instruction
If you have installed one or both of the old SGBox Windows packages Windows package Base and Windows package Advanced, you need to configure the following to avoid duplicate events generation:
Deactivate old packages’s classes
From LM->Configuration->Class uncheck the Active flag for the following classes:
- Windows logon events
- Windows user events
- Windows File Access
- Windows Audit Policy
- Windows GPO
After verifying that everything works as expected with the new Windows Audit package, you may want to remove old objects to keep the environment clean.
Clean old Classes
From LM->Configuration->Class delete the previously deactivated classes:
- Windows logon events
- Windows user events
- Windows File Access
- Windows Audit Policy
- Windows GPO
Clean old Dashboards
From the Dashboard list delete the following dashboards:
- Top 10 windows user logon events
- Windows User Operations
- Windows user related issue
Clean old Correlation Rules
From LCE->Rules delete the following rules:
- Windows User Added to Group
- Windows User Password Changed
- Windows User Password Reset
- Windows User Removed from group
- Windows Audit Policy Changed
Clean old Agent Configuration
From LM->Configuration->Agents remove the following configurations:
- Windows logon events
- Windows user events
- Windows Audit Policy
- Windows GPO
Clean old Windows packages
Identify and remove old Windows packages by clicking on the trash in the upper-right corner of each package box
Please note that deleting the package will not remove package objects, so the previous point by point cleanup is necessary.




