Search another article?
LCE → Rules
📝 Add and modify new rule
This page allows you to create and edit a rule.
A correlation rule is used to alert the admin when an event, or a series of events, occur in a specified time range.
✔️ Requirements:
- A mail server must be configured. Check the Configure a Mail server section for setup instructions.
- The pattern must belong to a specific class and be assigned to hosts.
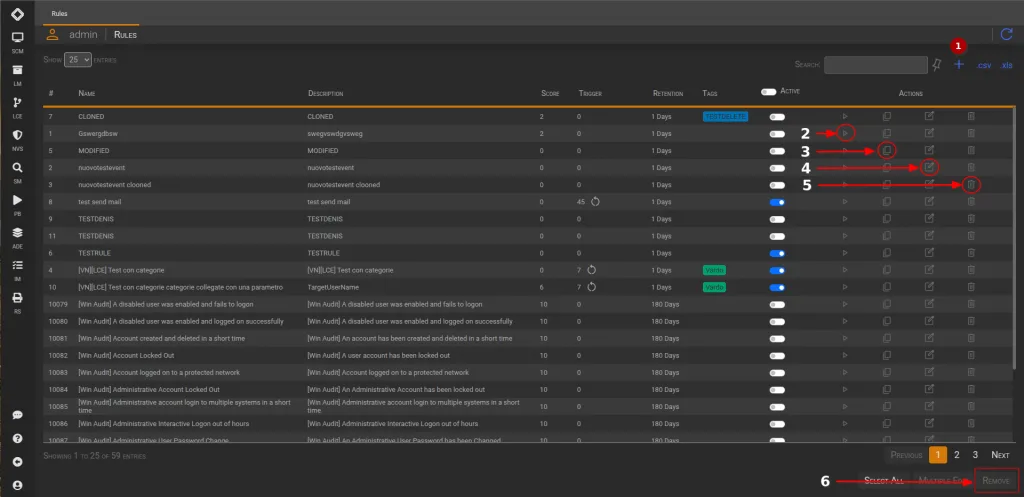
Using the SGBox web interface: SGBox → LCE → Rules
- The
plusicon opens the rule creation page. - The
playicon redirects the user to the edit page with atestview. - The
cloneicon opens a modal that allows the user to fill in the name and description fields. - The
editicon redirects the user to the edit page for modifications. - The
trashicon highlights the row in red and enables the delete button(6).
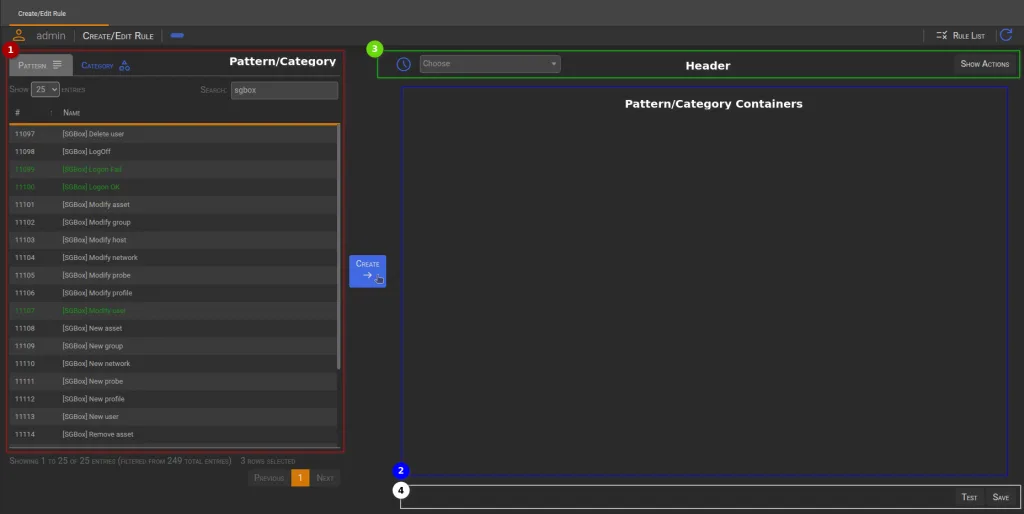
🛠️ Rule Creation Interface
- Left Section: Users can select one or more patterns to include in the rule. To choose a category, click on the
categorynavigation button. - Right Section (
Pattern/Category Containers): Displays selected elements with their associated parameters. Categories show only common parameters among patterns. - Header Section: Defines time intervals and shows available actions triggered by the Rule Engine.
- Bottom Section: Contains the
TestandSavebuttons.
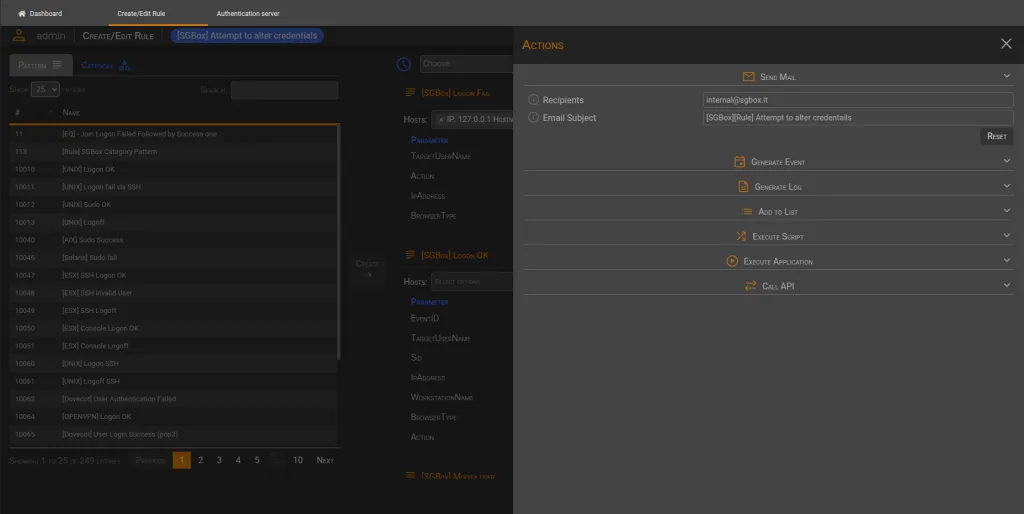
Clicking on the Show Actions button opens a sidebar displaying the available actions.
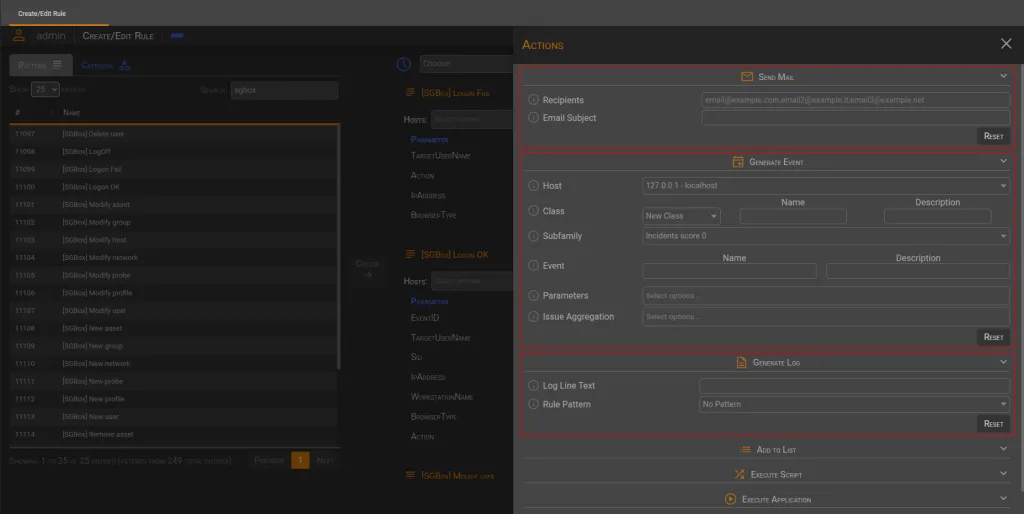
🚀 Actions
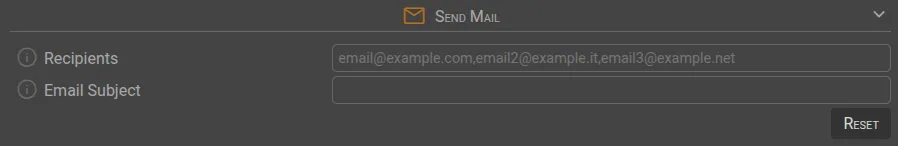
✉️ Send Mail
| Parameter | Description |
|---|---|
Recipients | Enter a list of valid email addresses separated by commas. |
Email Subject | When triggered, an email with the specified subject will be sent to all recipients. |
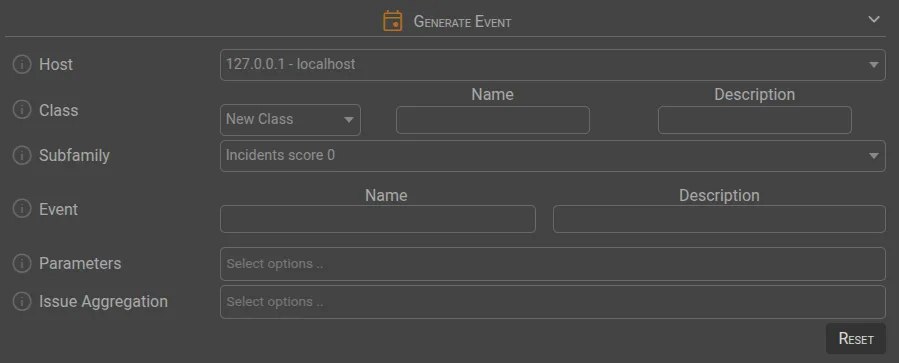
🗓️ Generate Event
| Parameter | Description |
|---|---|
Host | The event will be registered using localhost or the host associated with the event. |
Class | The selected class will be linked to the generated event. You can create a new class if needed. |
Subfamily | The selected subfamily will be associated with the event. The rule inherits its score. |
Event | Specify the name and description of the event. |
Parameters | Select up to 10 parameters to include in the event. Parameters from different patterns/categories cannot be duplicated. |
Issue Aggregation | Refers to the IM Module. |
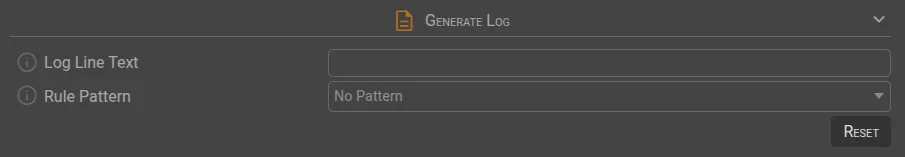
✍️ Generate Log
| Parameter | Description |
|---|---|
Log Line Text | Creates a log entry in SGBox upon rule trigger. View logs via LM → Analysis → Historical Search. |
Rule Pattern | Displays a dropdown with pattern parameters, allowing values to be assigned. |
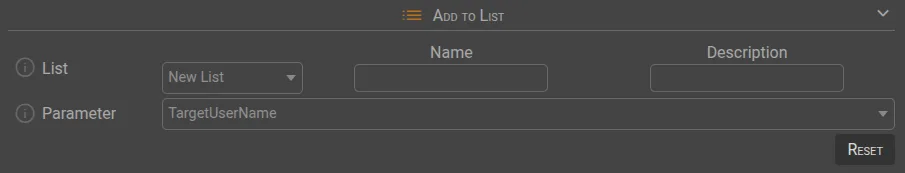
📋 Add To List
| Parameter | Description |
|---|---|
List | The selected pattern will be added to the list if not already present. |
Parameter | The parameter to add to the selected list. |
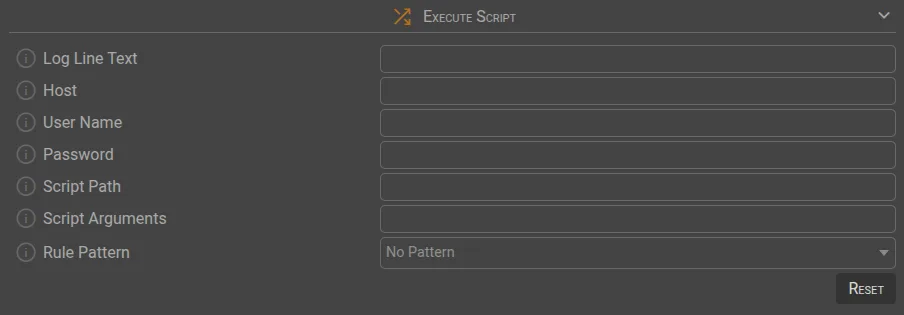
</> Execute Script
| Parameter | Description |
|---|---|
Log Line Text | Creates a log entry in SGBox when the rule is triggered. View logs via LM → Analysis → Historical Search. |
Host | Specify the host (IP address or hostname) where the script is located. |
User name | Provide the username for access. |
Password | Provide the associated password. |
Script Path | Specify the script’s location. |
Script Arguments | Arguments passed to the script. |
Rule Pattern | Displays a dropdown with pattern parameters, allowing values to be assigned. |
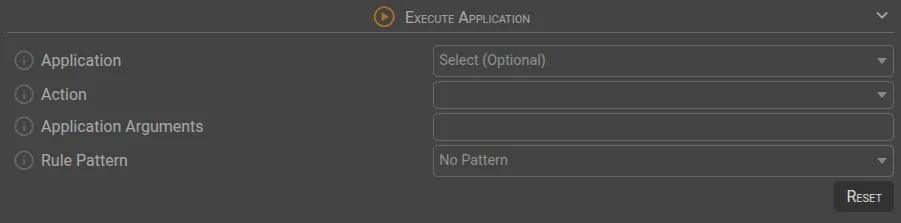
💻 Execute Application
| Parameter | Description |
|---|---|
Application | The selected application will execute upon rule trigger. |
Action | Defines the action the application will perform. |
Application Arguments | Arguments passed to the application. |
Rule Pattern | Displays a dropdown with pattern parameters, allowing values to be assigned. |
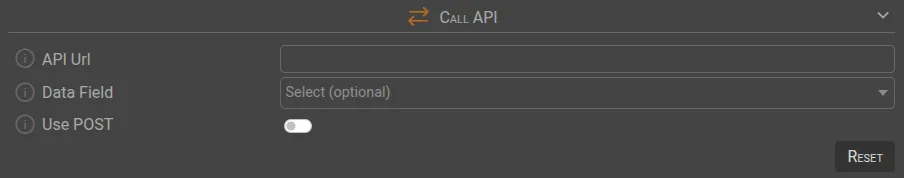
📲 Call API
| Parameter | Description |
|---|---|
API Url | The URL of the API to call when the rule is triggered. |
Data Field | The selected parameter will be sent via GET request by default. |
Use POST | If enabled, all parameters will be sent using a POST request in JSON format. |
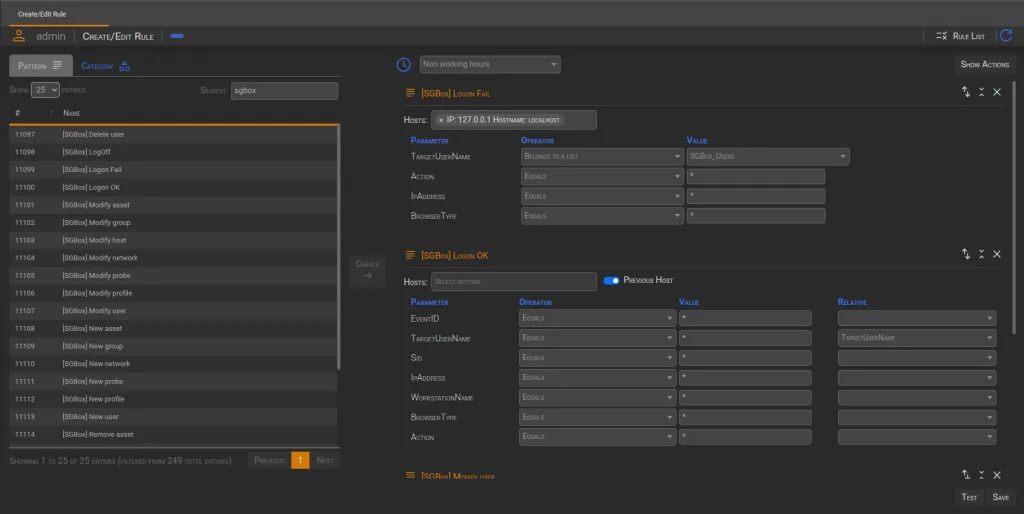
📌 Practical Example
This rule is designed to identify suspicious behavior where a failed login attempt to SGBox is immediately followed by a successful login and a user modification action. Such a sequence could indicate an unauthorized attempt to gain access and alter user credentials.
To make the detection more precise, the rule is configured to trigger only outside regular working hours by setting the time interval to Non-Working Hours. Additionally, it applies only if the access attempt is made by a specific user listed in a predefined group. The first pattern is restricted to localhost, meaning only login attempts on the local machine are considered relevant.
To ensure the integrity of the detection process, the rule verifies that all events originate from the same machine by enabling the Previous Host option. This prevents unrelated events from being linked together incorrectly. Furthermore, the Relative Column is used to maintain consistency in event parameters, ensuring that the entire sequence follows a logical flow before triggering an alert.
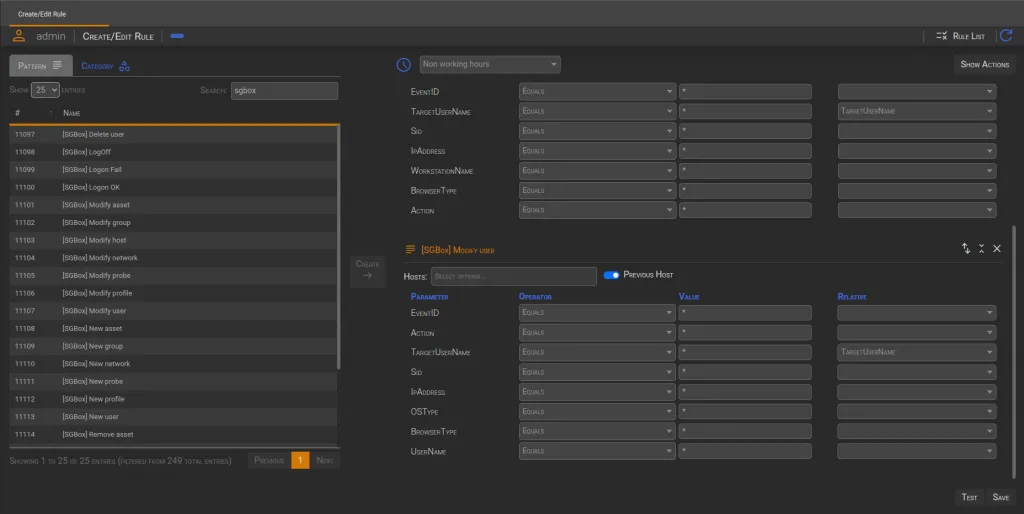
At this point, the rule must be saved. By clicking the Save button in the Bottom Section, a modal window will appear with the following fields:
| Name | The name of the rule, which can be up to 255 characters long. This field is required. |
| Description | A description of the rule, which can be up to 255 characters long. This field is also required. |
| Score | The value inherited from the subfamily when the Generate Event action is set. Otherwise, it will default to 0. |
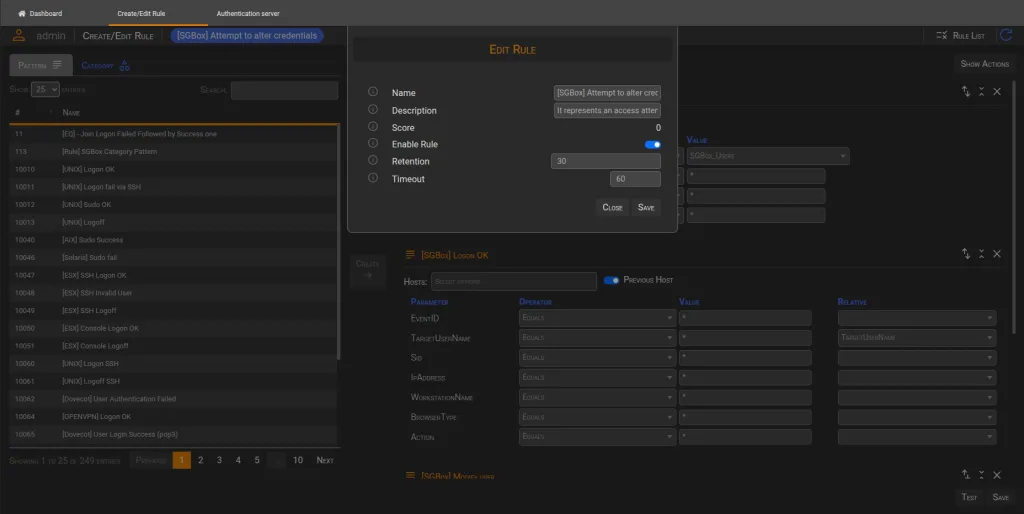
| Enable Rule | If set to true, the Rule Engine will analyze the event of this rule to determine when to trigger it. |
| Retention | Defines after how many days the rule’s history will be deleted (this value is displayed on the main page). |
| Timeout | This value specifies the number of seconds in which the event chain must occur. |
After configuring these parameters, you can confirm the operation and save the rule.
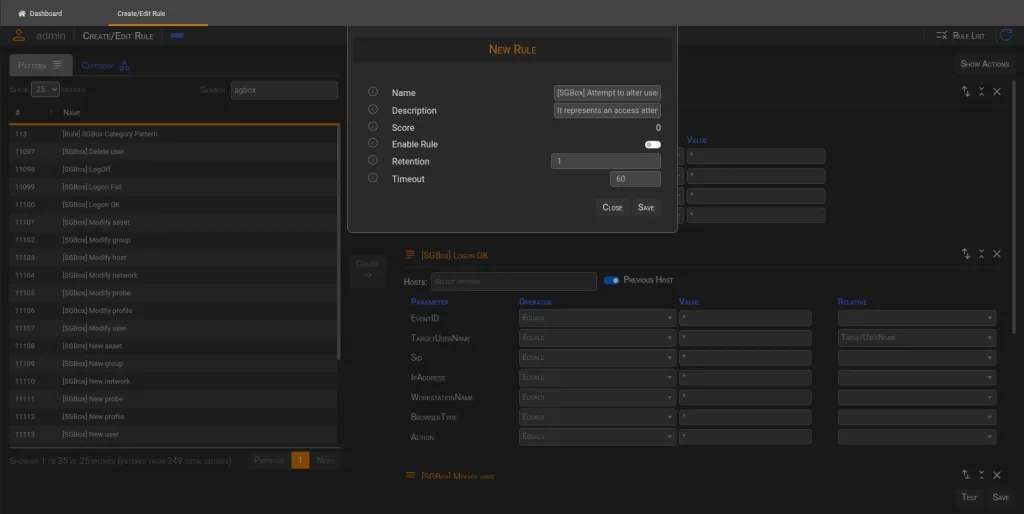
After saving the rule, the next step is to set an action and notify the administrators when the rule is triggered. To do so, you will need to configure the Send Mail action and save the entire rule.
Once the action is set, it is important to enable the rule so that it can be considered by the Rule Engine. Additionally, the retention value must be configured appropriately.
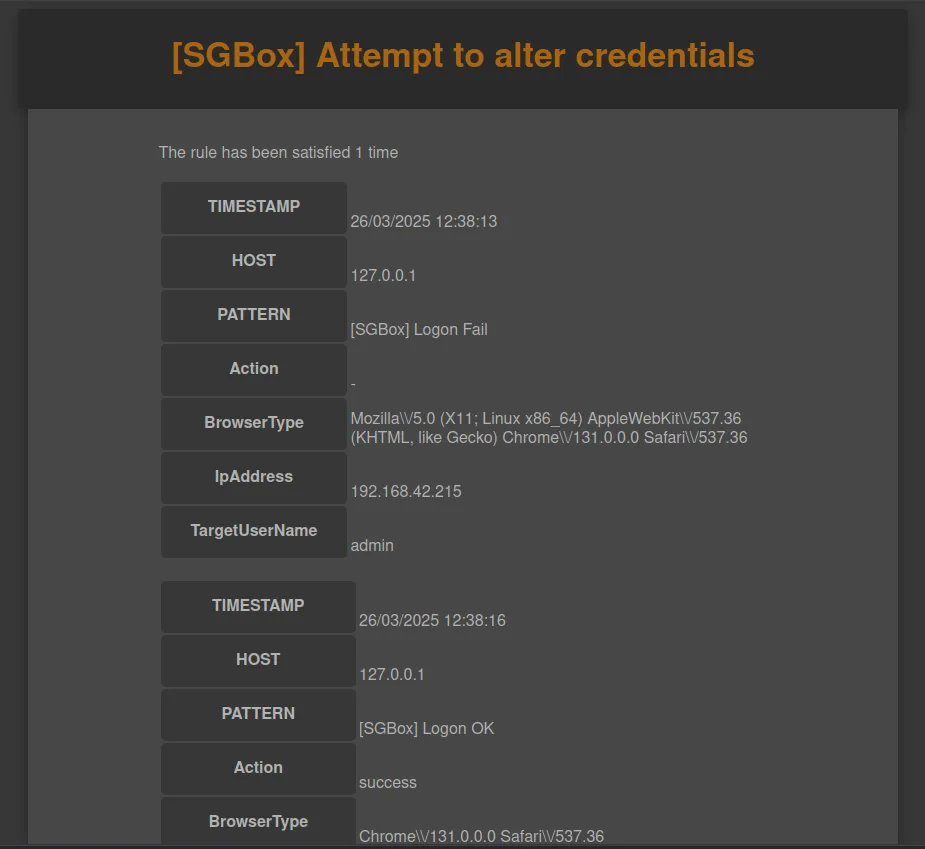
Here is an example of the email that the administrator will receive once the rule is triggered. The email includes the count of the times the rule has been triggered, as well as all relevant patterns and their details, providing the necessary information to ensure proper understanding of the event that occurred.
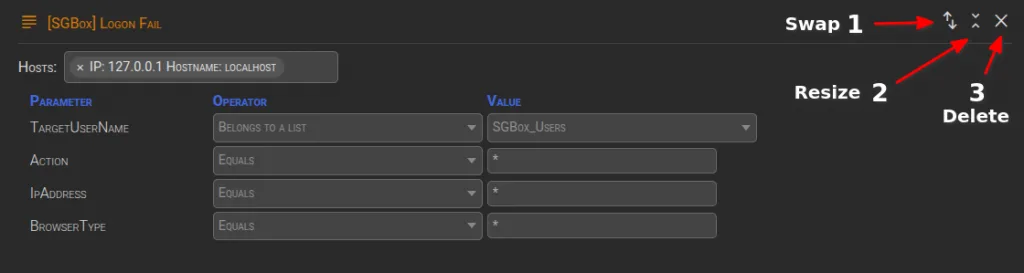
➕ Additional Actions:
- Swap: Swaps the container with the next selected one.
- Resize: Shrinks the container, displaying only the pattern name.
- Delete: Removes the pattern from the rule.
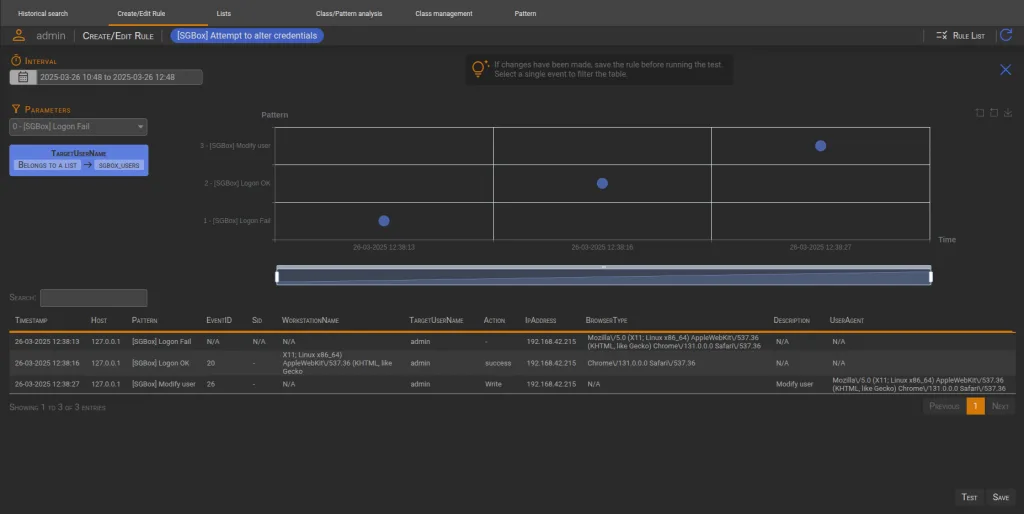
🔎 Test View
The Test View provides a way to preview events that match the previously defined rule flow. You can access this view by clicking the Test button. In essence, when one or more triggers occur, this view allows you to verify the corresponding events.
The page is divided into two main sections:
- Upper Section: Displays an intuitive chart that visually represents the event flow.
- Bottom Section: Lists the events along with their parameter values.
Users can adjust the time range to refine their analysis. However, it is important to note that rules are a powerful tool—using an excessively wide time range may result in long processing times.
When filters are applied, they appear on the left side of the interface, as shown in the image below. Otherwise, the chart expands to occupy the full available space.
Clicking on an event in the chart automatically filters the table below to display relevant details.
- N/A indicates that the pattern does not collect that specific parameter.
- Please note: To ensure an accurate test, make sure that the latest changes have been saved before executing the test.
🔧 Operators
The various operators are explained below:
| Operator | Description |
|---|---|
Equals | Matches values that are exactly the same. |
Differs | Matches values that are different. |
Greater than | Matches values that are strictly greater than the specified value. |
Lower than | Matches values that are strictly lower than the specified value. |
Greater or equal | Matches values that are greater than or equal to the specified value. |
Lower or equal | Matches values that are lower than or equal to the specified value. |
Contains a substring | Matches values that include a specified substring. |
Belongs to a set | Matches values that exist in a predefined set. |
Does not belong to a set | Matches values that do not exist in a predefined set. |
Belongs to a network | Matches IPs that are within a specified network range. |
Does not belong to a network | Matches IPs that are outside a specified network range. |
Belongs to a time range | Matches values that fall within a specific time range. |
Does not belong to a time range | Matches values that fall outside a specific time range. |
Belongs to a set - regexp | Matches values that conform to a regular expression within a predefined set. |
Does not belong to a set - regexp | Matches values that do not conform to a regular expression within a predefined set. |
Belongs to a set - regexp (case insensitive) | Matches values (case insensitive) that conform to a regular expression within a predefined set. |
Does not belong to a set - regexp (case insensitive) | Matches values (case insensitive) that do not conform to a regular expression within a predefined set. |
Regular expression search | Matches values using a specified regular expression. |
Regular expression search (case insensitive) | Matches values using a case-insensitive regular expression. |
host:port corresponds to a vulnerable host:port | Matches hosts and ports that are identified as vulnerable. |
host:port is associated with a known vulnerability | Matches hosts and ports linked to documented vulnerabilities. |
This host has been tested with NVS module | Matches hosts that have been analyzed using the NVS module. |
host:port is down | Matches hosts or ports that are unreachable. |
host:port is up | Matches hosts or ports that are active and reachable. |
A value in left set belongs to a value in right set | Matches when at least one value from the left set is present in the right set. |
This value has a reputation | Matches values that have a known reputation score. |
Belongs to a list | Matches values that exist in a predefined list. |
Does not belong to a list | Matches values that do not exist in a predefined list. |
Is longer than | Matches values that exceed a specified length. |
Is shorter than | Matches values that are below a specified length. |
Belongs to a list (exact match) | Matches values that exactly match an entry in the list. |
Matches with list | Matches values that have at least one common element with a predefined list. |
Match with regex list | Matches values against a list of regular expressions. |




