Search another article?
Syslog configuration on ESET
Following the steps to send logs from ESET (on-premise and Cloud) console to SGBox.
If you have a Syslog server running in your network, you can Export logs to Syslog to receive certain events (Detection Event, Firewall Aggregated Event, HIPS Aggregated Event, etc.) from client computers running ESET Endpoint Security. You can also configure ESET PROTECT Server to send Notifications to your Syslog server.
–> To enable Syslog server:
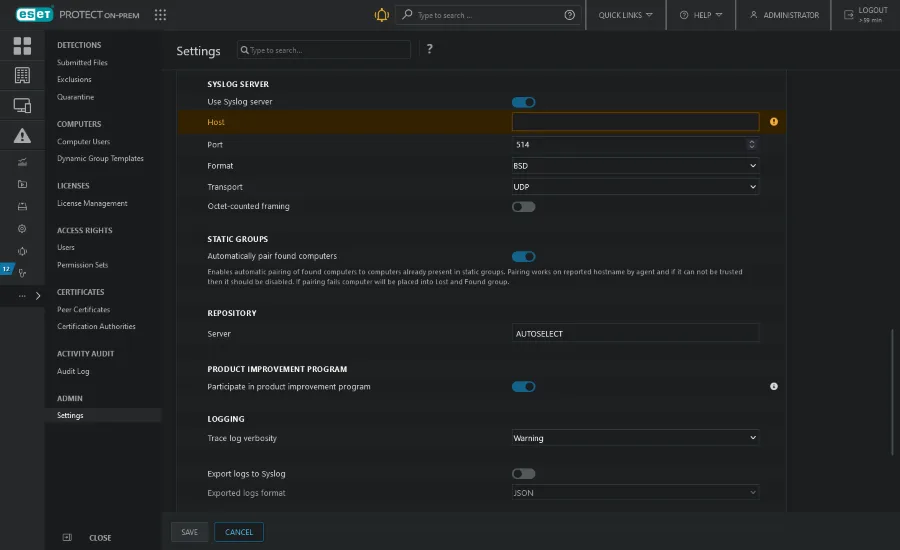
- Navigate to More > Settings > Advanced Settings > Syslog Server and click the toggle next to Use Syslog server.
- Specify the following mandatory settings:
- Host (IP address or hostname of the destination for Syslog messages)
- Port number (default value is 514).
- Format of the log: BSD (specification), Syslog (specification)
- Transport protocol for sending messages to Syslog (UDP, TCP, TLS)
- Scroll down to Logging and enable the Export logs to Syslog toggle.
After making changes, click save.
If you have a Syslog server running in your network, you can Export logs to Syslog to receive certain events (Detection Event, Firewall Aggregated Event, HIPS Aggregated Event, etc.) from client computers running ESET Endpoint Security.
To enable the Syslog server:
- Click More > Settings > Syslog and click the toggle next to Enable Syslog sending.
- Specify the following mandatory settings:
- Click More > Settings > Syslog and click the toggle next to Enable Syslog sending.
- Specify the following mandatory settings:
- Format of payload: CEF
- Format of envelope of the log BSD (specification), Syslog (specification)
- Minimal log level Information, Warning, Error or Critical
- Event type of logs—Select the type of logs you want to include (Antivirus, HIPS, Firewall, Web protection, Audit Log, Blocked files, ESET Inspect alerts).
- Destination IP or FQDN of TLS-compatible syslog server: IPv4 address or hostname of the destination for Syslog messages
- Validate CA Root certificates of TLS connection: Click the toggle to enable the certificate validation for the connection between your Syslog server and ESET PROTECT. After enabling the validation, a new text field will be displayed where you can copy and paste the required certificate chain. The server certificate must meet the following requirements:
- The whole certificate chain in PEM format is uploaded and saved in the Syslog export configuration (this includes root CA, as there are no built-in trusted certificates)
Your Syslog server’s certificate provides a Subject Alternative Name extension (DNS=/IP=), in which at least one record corresponds to the FQDN/IP hostname configuration.
You need: the certification authority version 3 (and later) with the Basic Constraints certificate extension to pass the validation. The validation of TLS connections applies only to the certificates. Disabling the validation does not affect the TLS settings of ESET PROTECT.
The regular application log file is constantly being written to. Syslog only serves as a medium to export certain asynchronous events, such as notifications or various client computer events.
After making the applicable changes, click Apply settings. The configuration becomes effective in 10 minutes.
For more information visit these links:




