Search another article?
Configure Threat Intelligence Queries
This article explain how to create a Threat Intelligence Query, that allows you to obtain simply the process of an Events Query to search a value in the list and take an action. In this way, queries can be used like LCE rules or sensors. Can be scheduled to run every minute on a time interval, performing actions when they found results. The available actions are Send Email, Generate Event, Add a parameter to a list.
Requirements:
- SGBox version 5.3.1
From SGBox menu, go to LCE > Threat Intelligence Queries. Click on New Query
A guided interface is available to build specific queries to search for a parameter in any list. A time interval can be set too. In the following example, we get all MS-Windows admin users logons during non-working hours.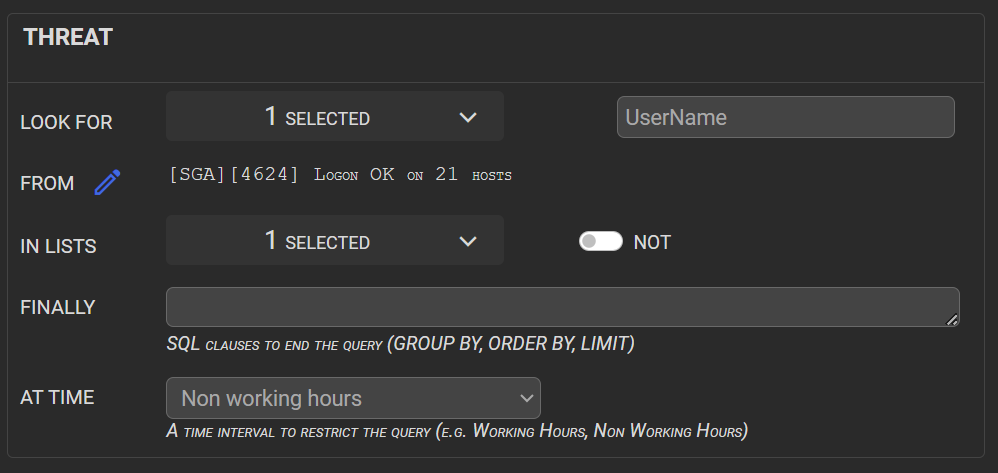
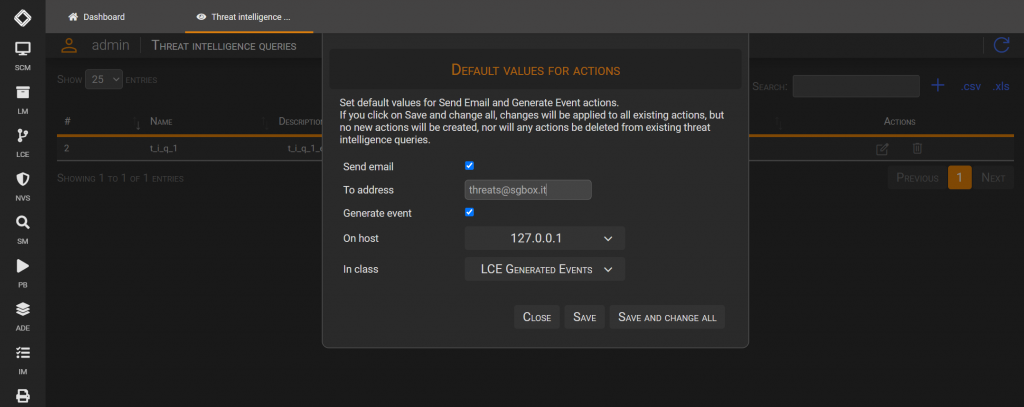
By default, Threat Intelligence Queries are scheduled and send an email and generate a new event every time they found any result.
Actions can be customized for each query, and default values can be edited by clicking the button DEFAULT VALUES on the page listing the Threat Intelligence Queries.