SGBox Platform: Next Generation SIEM & SOAR
We are excited to welcome you to the SGBox blog, a space dedicated to delving into topics related to cybersecurity solutions. Here, you will find updates, industry trends, and in-depth information about SGBox products, all with the aim of providing clear and defined information to make the world of cybersecurity more accessible.
In this article, we introduce our platform, defining its key features and functionalities.
What is SGBox?
SGBox is a modular and scalable Next Generation SIEM & SOAR platform designed to make the management of ICT security easy and efficient.
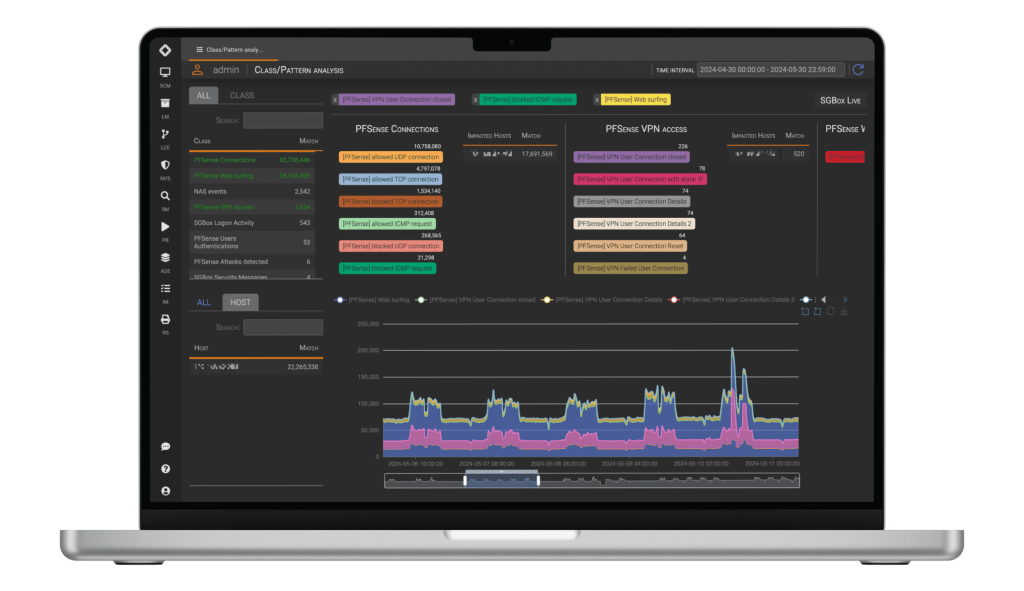
SGBox provides all the necessary tools to protect against any cyber threat and gain a comprehensive insight into the security status of your IT infrastructure through intuitive reports and dashboards.
Security event data is collected in compliance with privacy regulations. All logs are encrypted and made immutable to ensure their integrity.
The SGBox platform is suitable for safeguarding the infrastructure of organizations of all sizes, including small, medium, and large enterprises, and it also finds application in the Public Administration sector.
What does “Next Generation” mean?
“Next Generation” refers to a platform capable of processing a large amount of data and correlating it promptly.
The platform combines advanced data analysis and correlation features provided by SIEM (Security Information and Event Management) with those of orchestration and automation of response provided by SOAR (Security Orchestration Automation and Response).
The synergy between these two security areas provides advanced protection across the attack surface by detecting threats and proactively responding to security incidents.
Modules of the SGBox Platform
One of the distinctive features of SGBox is its modularity. The platform consists of different modules that work in synergy and can be easily integrated according to the specific security needs of an organization.
Below are the modules that make up the platform:
- SIEM (Security Information and Event Management): this is the cornerstone of the platform, allowing the collection, correlation, and analysis of information from security devices to respond promptly to attacks and generate security status reports.
- LOG MANAGEMENT: the Log Management function collects and classifies “logs,” which are information about operations performed by an IT system.
- EVENT CORRELATION & RESPONSE SYSTEM: this module correlates acquired information and creates correlation rules to detect potentially dangerous attacks.
- ACTIVE DIRECTORY AUDITOR: it monitors the state of Active Directories, enabling tracking of user access (e.g., to specific folders on a NAS) and monitoring their activities. This module provides Windows-compatible functionalities.
- USER BEHAVIOR ANALYTICS (UBA): it analyzes the activities of all users to determine if they pose a threat with their activities (e.g., browsing malicious websites) and provides reports on abnormal behavior. In this case, automatic countermeasures are taken to block the user for a period, such as restricting access to a network.
- THREAT INTELLIGENCE FEED: it gathers security information from an external, generally open-source feed, collecting security information in Indicators of Compromise (IoC) and correlating data to produce reports and alerts.
- NETWORK VULNERABILITY SCANNER: this module provides information for an overall assessment of cyber threats to a specific device. Following the scan, a report is generated on multiple levels (specific or a global snapshot) to make the client aware of network vulnerabilities. All vulnerabilities are classified with a severity score (CVE).
- ADVANCED EVENT SEARCH: this module is useful for monitoring resource status, such as RAM, CPU, disk space, and, in general, for resolving IT network issues.
- INCIDENT MANAGEMENT: this function allows for the management of incidents and anomalies found in other SGBox modules. It provides an intuitive graphical view that identifies incident structure and their state of evolution. It also offers ticketing for technical support.
- SOAR (Security Orchestration Automation and Response): this is another core function that complements SIEM. SOAR introduces the concept of orchestrating and automating response activities, eliminating the need for human intervention and minimizing response times to attacks.
- CLOUD SIEM: Cloud SIEM is one of the latest ways to use SIEM. It allows for agile and flexible cybersecurity threat mitigation through SGBox’s Cloud in “As a Service” mode.
- FILE INTEGRITY: this module verifies that data remains unaltered and unauthorized manipulation. It is a crucial component that, in synergy with SIEM, contributes to detailed monitoring of activities.




